What is LoginLlama?
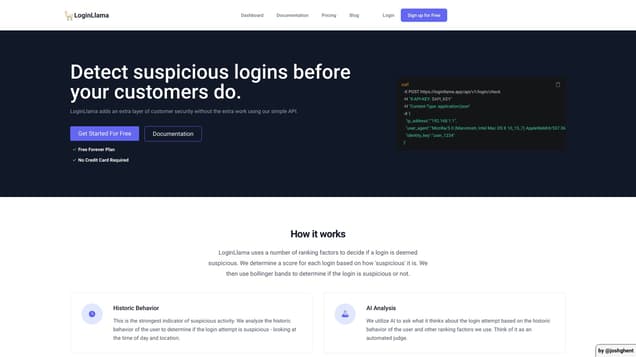
LoginLlama is a comprehensive set of APIs created to identify and address questionable login activities, bolstering customer security measures for online enterprises. This powerful tool empowers developers to safeguard their users against malicious hackers and thwart any unauthorized attempts to access confidential information.
Information
- Financing
- $220.00M
- Language
- English
- Price
- Freemium
Pros VS Cons
- Pros
- LoginLlama is an API-based tool that offers comprehensive features such as historic behavior analysis, request origin examination, and customizable sensitivity controls to prevent unauthorized access and detect various types of attacks, making it suitable for large enterprises with developer-friendly design and adherence to privacy policies.
- Cons
- However, it has limitations such as a limited free request limit, complex API integration, lack of multi-factor authentication, IP whitelist/blacklist feature, user interface, multi-user support, account recovery, mobile app, and limited support options, which may pose challenges for some users.
Freework.ai Spotlight
Display Your Achievement: Get Our Custom-Made Badge to Highlight Your Success on Your Website and Attract More Visitors to Your Solution.
Website traffic
- Monthly visits3.03K
- Avg visit duration00:02:24
- Bounce rate1.08%
- Unique users1.91K
- Total pages views8.89K
Access Top 5 countries
Traffic source
LoginLlama FQA
- What is the pricing for LoginLlama?

- How does LoginLlama prevent unauthorized access?

- What are the top login threats that LoginLlama combats?

- What is the historic behavior analysis used by LoginLlama?

- What are the available integrations for LoginLlama?

LoginLlama Use Cases
Enhance customer security effortlessly by preventing fraudulent logins with our simple API.
Effortlessly Secure Your App
Get Started For Free
Free Forever Plan — No Credit Card Required
Through multiple ranking factors, LoginLlama evaluates login attempts, scoring each based on its 'suspiciousness' level.
This is the strongest indicator of suspicious activity. We analyze the historic behaviour of the user to determine if the login attempt is suspicious.
We utilize AI to ask what it thinks about the login attempt based on the historic behaviour of the user and other ranking factors we use. Think of it as an automated judge.
We look at the IP address of the login attempt and information about it. For example, we check if that IP address is from known VPN providers or a TOR exit node.
Looking at the user agent we can determine the users browser and operating system. This data is used to check against where the customer usually logs in.
Phishing Attacks